Codes versus Code Breakers
Published on August 24,2017

A brain as little as a squirrel’s is an adequate intuition to put to test the brawn of 10 hunters, save that of their 20 dogs. The above is the mirror image of a fight, a war, and most importantly, leadership. How else are the world’s superpowers able to control the third world countries, if not through the immense intelligence they possess? Mathematicians won world-war II, mathematicians broke the Jap code, Allan Turing (mathematician) broke the Enigma, and it was pure intelligence (from Sun Tzu) that won the Vietnam War. Were it not for intelligence, World War II could have been prolonged for two more years (who knows the resultant effects of the world’s bloodiest war?). For sure, what controls this world is intelligence and the secrecy with which it is possessed. This is the subject of this article: - the science of secret information storage and communication (cryptography).
Starting from political power, the world’s largest economy and superpower, the US, has numerous known intelligence societies including the CIA and the NSA. Russia has its KGB; and the world’s second largest economy, China, has its secret society so secret that its name is not even known to the public. From political power, we move to the revolutionary Internet. Websites of late, are ceasing to use HTTP alone and are migrating to https. But what advantage does the latter have over the former? Http stands for hypertext transfer protocol, while https stands for secure hypertext transfer protocol. Https uses a secured communication channel in which data and its corresponding metadata (data about data) are encrypted i.e. the data is encoded/hidden from plain view such that even if it is intercepted by a third party (Eve’s dropper) the data gained theretofore is unfathomable by them hence useless. Consider still the large anonymous network forming the largest network of any kind in the world, the dark web. Its backbone is entirely dependent on secret communication. In addition, the new technology of Cryptocurrency, money can now be exchanged without the traders being known. Finally, to the root of the new generation, social media such as WhatsApp has incorporated this amazing technology. But what is really behind all these?
What really is cryptography?
Cryptography is the science of secret communication. In the early years of the Roman Empire, Julius Caesar, when he needed to communicate a strategic message to his army generals, he ensured that his enemies were kept in the dark even if they intercepted his messages. In this science, there are some major terms that you ought to understand. To begin with, there is the plain text: This is the message written in the plain language that the crowd can understand. Secondly, there is the encryption algorithm. This is the mathematical or the scientific technique/ formula that transforms the plain text into the encrypted text. The encryption algorithm houses what is called the encryption key. This is a very important part of this science and, as you guessed, it is a key that will be used to ‘open’ the encrypted text back to the plain text. The encrypted text is called the cypher text. Mathematically: plain text + encryption algorithm + key------ →cipher text.
The earliest forms of cryptography were recorded to have been used by the Greek’s Spartans and the Roman emperor Julius Caesar. The Spartans used a form of cryptography known as Scytale, where a piece of paper would be wrapped around a pipe of a specific diameter, and the message would be would be written along the paper while still wrapped around the pipe. The paper would then be unrolled and the message would be ready for sending. If read while still on the pipe, the message is readable and could be understood, but once unrolled, it was jumbled up. This jumbling up is what cryptography is about. Take a look at the photo below.

Julius Caesar, on the other hand, used what is termed as a substitution cypher. In this form of cryptography, the letters in the alphabet were substituted with other letters of the alphabet by shifting by a number e.g. 3 in the case of Caesar cypher. Therefore letters A, B, C, and D would be shifted by three to D, E, F, and G. So a message like “attack at dawn” would be encrypted to “ .” can you believe that this simple form of cryptography was used for more than 800 years before it was broken by code breakers?
What is new in this science?
Human beings have proven to be too wise for every technique introduced by the code makers. Every time they are broken, even if it takes a century, it will eventually be broken. And that’s exactly why we now solely depend on the ‘mercy of enormous.’ The Advanced encryption standard (AES) and other very important encryption techniques depend on prime numbers and the ambiguity of factorizing them. This is the situation; if you have two very large prime numbers, it is very easy to multiply them and have the resultant very large prime number. It is however very difficult to factorize a very large number and obtain the two prime numbers used to form it. And this simple idea is what protects our very important infrastructures from being brought down. But what if that secret behind prime numbers, that still remains unknown to anyone, gets revealed to someone, then as a flash of light, our key infrastructures would be down by the hands of the code breakers.
The African situation: the importance of foreknowledge
We are lagging behind once again in the world’s major key resource. Knowledge and its application thereof. A well-educated African is indeed of a high intellect and that has been proven. Then where is the problem? I am a student of a major institution in East Africa and the frequency with which the term ‘cryptography’ is mentioned is just close to zero. In fact, I am the only one who mentions it to any friend of mine who can fathom its nature. The science is so hidden in Africa that even the books with the knowledge about the subject are lacking. You know what? The only reason why African nations fail in general is that of uneducated leaders, who can’t even do a successful project planning, let alone understand how important the field of cryptography is. And the only reason why Africa is still dearly enslaved is due to inadequate knowledge in major fields.
According to the father of military intelligence, Sun Tzu, the only way to beat your enemy successfully is to have foreknowledge. I.e. knowledge about his next and future moves, only then can one prepare adequately. Had the Allies of World War II lacked the British’s Hut 8, Bletchley Park, then Hitler’s moves would have gone undetected. Thanks to Allan Turing, the Cryptography machine, the Enigma, was broken. And so the war ended in 1945 after a lot of blood was shed. In your country alone are there Hut 8, Bletchley Park equivalents? This Hut 8, Bletchley Park housed mathematic geniuses who used their skills to break the codes that were formed using mathematical algorithms. As Africans, we rely on what is already made by other nations that our success depends on theirs. In the first place, how many expatriates do we have in this field? If Kenya has 1000 computer science registered professionals, then there are about ten for cryptography.
A call for code breakers
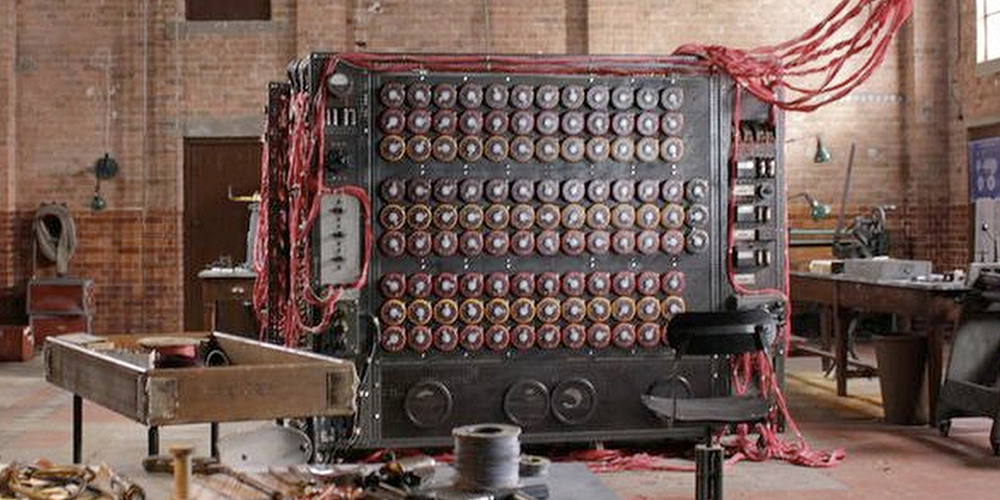

If only you could have seen the size of the Enigma machine and compare it to that built by Allan Turing to break the former, then it would be clear to you that immense work is done when breaking a code that when ciphering a code. On the above image, the left shows Allan Turing's bombe machine and to its right is the German's Enigma to be broken. A cryptographer would only need to design an algorithm, a very strong key, and a secure infrastructure over which it will be used. A code breaker, on the other hand, would need to master both the art of making the code and the art of breaking the code. These are all covered in the subject of CRYPTOLOGY. So many students have enrolled for the field of computer science but close to none have done the same for the field of cryptography. The reason is that the field is unknown to them let alone being offered in their respective institutions. This is a call to African governments to introduce this amazing scientific field. Let them worry not about the mathematics; that even I alone can fathom. All that is needed is an open field: - resources for knowledge, and fields of application, plus adequate payment. If my country even lacks adequate expatriates in the field of cyber security, how then are we going to face the future where everything is in the cyber realm including surgery robots?