WannaCry: the digital weapon from the chief hacker's vault
Updated on October 23,2022
Code named ‘WannaCry’, ‘WannaDecryptor’, ‘WannaCrypt’ or just the layman’s ‘YouDontWannaCry’, it is a ransomware of its kind (from the Ransom.CryptXXX family) that hit the whole world to its knees on Friday the 12th of May, 2017.
Security researchers and professionals have labelled it the largest ransomware assault on record while at the same time calling it “the atom bomb of ransomware.”
I would call it a digital weapon pulled directly from the ‘chief hacker’s vault of hacking manuals and blueprints.’ And were you to ask any security researcher (at one of those institutions bisecting the malware like Malwarebytes) the question: “what keeps you awake all night?” the answer would have been unconsciously, “Wannacry.”
Here is why it is a digital superstorm. It is the first time a cyber weapon developed by the N.S.A (notorious for its I.T expertise and doings), funded by American taxpayers (directly and indirectly with and/or without their knowledge) and stolen by an adversary, had been unleashed by cybercriminals against patients, hospitals, businesses, governments and ordinary citizens.
The effects have far spread worldwide. Having read the first article on what ransomware is and how they work. This article will analyse its origin, prey, propagation, behaviour and mechanisms of camouflage, effects so far, and the preventive (not cure) measures.
Origin
The roots of its genealogy are traced back to the Obama administration when the White House created a process to review software vulnerabilities discovered by intelligence agencies like the N.S.A and C.I.A.
Just like your country’s government would, they solely determined which of the vulnerabilities should be stockpiled for future offensive or defensive cyber operations and which should be reported to the respective companies so that they could be fixed.
According to the government in question, only a small fraction of the vulnerabilities was retained; Microsoft windows’ SMB vulnerability was among these kept.
Secured under the N.S.A.’s “Tailored Access Operations” unit, which infiltrates foreign computer networks (as expected, the unit has since been renamed.), the ultimate hacking tool (named Eternal Blue) for exploiting these depots of vulnerabilities was stolen probably by a group of hackers calling itself the “Shadow Brokers”.
Later on, in 2016, the group Shadow Hunters began to post these software tools that would exploit the vulnerability in Microsoft Windows servers.
On Friday, 12th May 2017, hackers (not yet known) exploiting these stolen hacking tools executed damaging cyber attacks that hit dozens of countries worldwide, leveraging heavy burdens on the victims.
A case study is Britain’s public health system which was denied access to its computers, forcing them to send patients away. This saw disruptions rippling through at least 36 hospitals, doctors’ offices and ambulance companies across Britain.
The prey and methods of spread
The malware exploits a Windows SMB Server vulnerability. This renders all unpatched Windows Systems at risk of infection.
If you use any version of Windows, including Windows XP, Vista, 8, Server 2003 and 2008, except Windows 10, with SMB protocol enabled, then you are at risk.
If you are using Windows 10 Creators Update (1703), you are not vulnerable to SMB vulnerability.
The malware is being circulated by email (see email phishing).
Targets hit were sent an encrypted, compressed file that, once loaded, allowed the ransomware to infiltrate its targets.
The fact that the files were encrypted ensured that security systems would not detect the ransomware until employees opened them, inadvertently allowing the ransomware to replicate across their employers’ networks.
Once infected, WannaCry also scans for other unpatched PCs connected to the same local network and scans random hosts on the wider Internet to spread itself quickly.
Once infected, you become a network node zombie (botnet) that simply helps in the propagation of this attack. For that reason, when a node is hit, it should be isolated from the network.
The next section is a bit technical. You can skip the next section, which discusses the effects and new developments if you are not interested in the more delicate details.
Technical details on the attack
C/O CERT-MU
- When the Trojan is executed, it drops the path files [PATH_TO_TROJAN] where the Trojan was originally executed.
- The Trojan then creates and sets some registry entries like HKEY_CURRENT_USER\ControlPanel\Desktop\"Wallpaper"=%UserProfile%\Desktop\!WannaCryptor!.bmp"
- The Trojan creates the following mutexes: Global\WINDOWS_TASKOSHT_MUTEX0, Global\WINDOWS_TASKCST_MUTEX
- The Trojan then terminates the following processes using taskkil /f /iml: sqlwriter.exe, sqlserver.exe, Microsoft.Exchange.* , MSExchange*
- It then searches for and encrypts files with the following extensions:.123, .3dm, .3ds, .3g2, .3gp, .602, .7z, .ARC, .PAQ, .accdb, .aes, .ai, .asc, .asf, .asm, .asp, .avi, .backup, .bak, .bat, .bmp, .brd, .bz2, .cgm, .class, .cmd, .cpp, .crt, .cs, .csr, .csv, .db, .dbf, .dch, .der, .dif, .dip, .djvu, .doc, .docb, .docm, .docx, .dot, .dotm, .dotx, .dwg, .edb, .eml, .fla, .flv, .frm, .gif, .gpg, .gz, .hwp ,.ibd, .iso, .jar, .java, .jpeg, .jpg, .js, .jsp, .key, .lay, .lay6, .ldf, .m3u, .m4u, .max, .mdb, .mdf, .mid, .mkv, .mml, .mov, .mp3, .mp4, .mpeg, .mpg, .msg, .myd, .myi, .nef, .odb, .odg, .odp, .ods, .odt, .onetoc2, .ost, .otg, .otp, .ots, .ott, .p12, .pas, .pdf, .pem, .pfx, .php, .pl, .png, .pot, .potm, .potx, .ppam, .pps, .ppsm, .ppsx, .ppt, .pptm, .pptx, .ps1, .psd, .pst, .rar, .raw, .rb, .rtf, .sch, .sh, .sldm, .sldx, .slk, .sln, .snt, .sql, .sqlite3, .sqlitedb, .stc, .std, .sti, .stw, .suo, .svg, .swf, .sxc, .sxd, .sxi, .sxm, .sxw, .tar, .tbk, .tgz, .tif, .tiff, .txt, .uop, .uot, .vb, .vbs, .vcd, .vdi, .vmdk, .vmx, .vob, .vsd, .vsdx, .wav, .wb2, .wk1, .wks, .wma, .wmv, .xlc, .xlm, .xls, .xlsb, .xlsm, .xlsx, .xlt, .xltm, .xltx, .xlw, .zip
- Encrypted files have .WCRY appended to the end of the file names.
- The Trojan then deletes the shadow copies of the encrypted files.
- The Trojan drops the following files in every folder where files are encrypted: !WannaDecryptor!.exe.lnk,!Please Read Me!.txt. The contents of the! Please Read Me!.txt is a text version of the ransom note with details of how to pay the ransom.
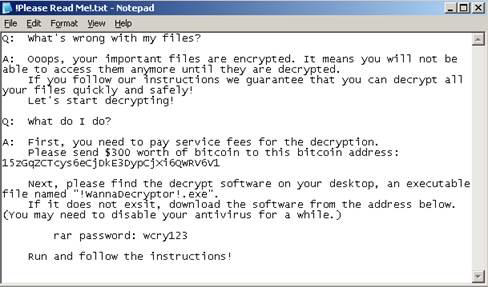
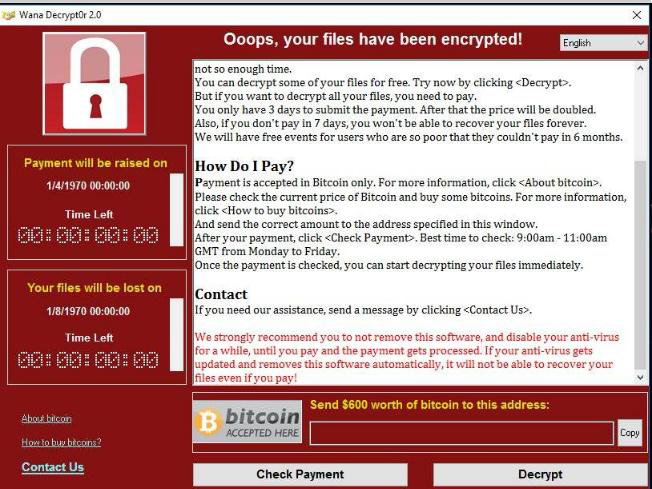
The Trojan downloads Tor and uses it to connect to a server using the Tor network. It then displays a ransom note explaining to the user what has happened and how to pay a ransom to recover files.
Effects and new developments
By late Friday, the attacks had spread to more than 74 countries by the day of the attack.
According to security firms tracking the spread, the trojan and had already hacked nearly 200,000 Windows PCs.
Kaspersky Lab, a Russian cybersecurity firm, said Russia was the worst hit, followed by Ukraine, India and Taiwan.
Reports of attacks also came from Latin America and Africa.
About 104 countries worldwide, including the U.K, Russia, Ukraine, India, China, Italy, and Egypt, have been affected by the end of the weekend.
South Africa leads the pack among the African countries affected, followed by Ivory Coast and Nigeria. Egypt, Algeria and Morocco complete the top six countries. At least 19 servers have been hit in Kenya. Angola, Mozambique, Tanzania, Niger and Tunisia have also been hit.
In Russia, the country’s powerful Interior Ministry had around 1,000 of its computers (which it described as less than 1 per cent of its total) infected. The ministry, overseeing Russia’s police forces, said technicians had contained the attack.
Corporate computer systems in many other countries — including FedEx in the United States, one of the world’s leading international shippers, and Spain’s Telefónica and Russia’s MegaFon telecom giant were also seriously affected.
The ransom to be paid started at its low of about $300 to unlock an individual computer. But the criminals designed their ransomware to increase the ransom amount on a set schedule and threatened to erase the hostage data after a predetermined cut-off time, raising the urgency of the attack and increasing the likelihood that victims would pay.
For close to the actual values of ransom paid so far, you can check the Twitter account @actual_ransom.
Even though a security researcher successfully found a way to slow down the infection rate, with Microsoft also releasing emergency patch updates even for unsupported versions of Windows, the researchers have detected some new versions of this ransomware, dubbed WannaCry 2.0, which the kill switch couldn’t stop.
Even worse, the new WannaCry variant is believed to be created by someone else and not the hackers behind the first WannaCry ransomware.
Preventive measures
- Install security updates, especially if using other versions of windows apart from Windows 10.
- Patch the SMB vulnerability (CVE-2017-0148) with the patch MS17-010, available here.
- Disable SMB. Even if you have installed the patches, you are advised to disable Server Message Block version 1 (SMBv1) protocol, which is enabled by default on Windows, to prevent against WannaCry ransomware attacks.
- Here is how to do it.
For Windows clients
- Go to Windows Control Panel and open 'Programs.'
- Open 'Features' under Programs and click 'Turn Windows Features on and off.'
- Now, scroll down to find 'SMB 1.0/CIFS File Sharing Support' and uncheck it.
- Then click OK, close the control Panel and restart the computer.
For Windows Servers
- Open Server Manager, click the Manage menu and select Remove Roles and Features.
- In the Features window, clear the SMB1.0/CIFS File Sharing Support check box and click OK to close the window.
- Restart the system.
- Enable Firewall & Block SMB Ports. Always keep your firewall enabled, and if you need to keep SMBv1 enabled, then just modify your firewall configurations to block access to SMB ports over the Internet. The protocol operates on TCP ports 137, 139, and 445 and over UDP ports 137 and 138.
What you can be sure of is that these attacks will continue. We’ll see copycats, and not just for ransomware, but other attacks. That’s why you hear of families of ransomware.
Even though Talwork has since been trying to educate the public on major IT security concerns, most of this knowledge has failed to reach its purpose destinations.
The reader is requested to be responsible with the knowledge gained heretofore by spreading the knowledge gained while doing the same for the source of knowledge.
The vulnerability seen so far is, however, a clear indicator of the need for an up game. It is a wake-up call for aspiring IT professionals, especially from Africa (Africa is extremely deficient in cyber-intelligent organisms, robots inclusive). Since this widely spread ransomware attack is neither the first nor the last one to hit users worldwide, prevention is always the key to protecting against such malware threats.