Ransomware analysis-into the roots of WannaCry
Published on May 17,2017

No one wants to be part of a story such as mine that follows. In January 2017, my computer screen was defaced with a very funny (yet annoying) beggar’s message demanding that I pay a sum of US$ 402. Failure to do so called for a permanent loss of my important files (my photos, electronic certificates, very important books and videos for my college study) which already has been encrypted. This was a Cerber ransomware attack. It all began after I downloaded a torrent for just an eBook with the pdf (portable document format) extension. On clicking the torrent link, it downloaded a folder. On complete download I opened the folder and found the file of my interest and opened it. As if nothing is wrong, the Adobe reader simply opened the document. I simply could not understand the language in which the document was written, it was in Russian language. I went back to the downloaded folder and opened the readme.txt text file. The instructions there were very clear and heart sinking. It read thereby: “Your Adobe Reader does not have the fonts necessary to open your document. To install the required fonts, click on the executable file in this folder.” I executed the executable (.exe) file by clicking on it. From that moment onwards, I could not easily navigate through my files; even the names of the specific files were randomized making it difficult to know what is what. It is annoying experience you don’t want to face, trust me. To help you avoid being a victim of such a scenario, I have prepared this article for you. In it we will, explore what a ransomware is, what forces are behind it, its method of manufacture, its distribution methodology, methods of operation. We will then analyse the WannaCry malware that has recently hit the world (all these genius minds) to its knees.
What is a ransomware?
The word ransomware is basically from two words, ransome, and malware. As you already know, a ransom is anything valuable e.g. money, that you pay in order to release something or someone from being a hostage (a better example of a ransom is that which is usually demanded by kidnappers so that they can release their hostage). Malware on the other hand is a malicious software. So in a nutshell, a ransomware is a malicious software that holds a user’s resources e.g. data and/or machine hostage (by encrypting the data or locking the machine hence denying the access to it or its very important resources) while demanding a ransom to be paid. Until it is paid, the user will not be able to access the held resources. It is often accompanied with threats to act on the user’s fears but some are real threats. The Cerber ransomware that attacked my machine threatened to delete files if I don’t pay the ransom within two days. The following image gives a timeline of major ransomware attacks experienced over the years.
The origin
Ransomware is entirely driven by encryption. Just to be sure we are on the same page, I would love to discuss what encryption is briefly. The first recognizable form of encryption was used by Julius Caesar. It is called Caesar cipher. Also known as a shift cipher, it is a substitution cipher where each letter in the original message (called the plaintext) is replaced with a letter corresponding to a certain number of letters up or down in the alphabet. That is to say, if you decide to use a shift of 3, then letter A becomes D, letter B become E, and so on. For example, here's the Caesar Cipher encryption of a message, using a right shift of 3.
Plaintext:
THE QUICK BROWN FOX JUMPS OVER THE LAZY DOG
Cipher text:
QEB NRFZH YOLTK CLU GRJMP LSBO QEB IXWV ALD
The process of converting a plaintext to ciphertext is called encryption.
Clearly, from the above example, it is very difficult for one to understand the cipher text as opposed to the plain text. If you had the cipher text only and you want the plain text, you have to own the key. The key, in this case, is the number 3. Using the key in converting the ciphertext back to the plaintext is referred to as decryption. Decryption without using the key is what most call code breaking and it involves techniques such as frequency analysis. The Caesar cipher above is just too simple to decode. Encryption techniques such as the shift cipher, hill cipher, RSA, RC4, advanced encryption standard (AES), wired equivalent privacy (WEP), WPA and WPA2 (the ones you use for encrypting your network communications) are some of the examples of encryption algorithms.
There are two variants of encryption, asymmetric and symmetric.
What does “asymmetric” mean and why does that matter? The defining characteristic of public key cryptography is the use of an encryption key by one party to perform either encryption or decryption and the use of another key in the counterpart operation. In symmetric-key algorithms, there is a single key used and shared between receiver and sender, thus the key used by the receiver and sender is “symmetric” because it is the same. The use of multiple keys in asymmetric public key cryptography allows ransomware to encrypt items on a system with a public key while never exposing the private key, thus keeping it secret. For ransomware, this is essential for “mangling” data files without exposing anything that someone could use to figure out how to undo the encryption. So you have to pay a ransom in order to get the key.
Methods of manufacture
Several new ransomware families have been coded in different programming languages, such as JavaScript, PHP, PowerShell, or Python. Attackers used these languages in an effort to evade detection by security products. A number of high-profile ransomware families have also begun to add features beyond the core functionality of locking devices or encrypting files. For example, CryptXXX Contains an additional feature that allows it to gather Bitcoin wallet data and send it to the attackers. Cerber is reportedly capable of adding the infected computer to a botnet which can be used to carry out distributed denial of service (DDoS) attacks. Chimera makes an additional threat in its ransom message. In addition to encrypting files, the malware threatens to post the victims files, including pictures and videos, on the internet. The adoption of these new techniques demonstrates how ransomware is continuously evolving to maintain its foothold and remain profitable.
The major advancement in their manufacture is that they are in the cloud, being offered as a service. The code name “Ransomware-as-a-Service” means that an affiliate (malware spreader) does not need any special programming skill, simply the willingness to spread the ransomware (typically through email botnets (a network of zombie/infected computers used to infect other computers) that are easy for a non-programmer to set up). The affiliate can sign up as an affiliate and simply download a customized ransomware binary. The malware has custom payment instructions and payment credentials and allows the affiliate to easily take part in the ransomware game.
Ransomware authors are now officially organized gang, and they have made it easy for wannabees and affiliates to participate in their crime chain and spread this malware. The automate ransomware business model includes sophisticated tools such as the telemetry dashboard that reports all kinds of useful information, such as the price for the campaign, the amount paid per binary, the operating system that is infected, time zone, and more. Affiliates now have detailed capabilities to see how effective their campaigns are and can tune their efforts to extract the maximum benefit for themselves (without leaving the comfort of their homes).
The life cycle
Like a normal living entity, malware have a life cycle.
The first step is distribution: Ransomware uses standard methods of distribution. Generally it is spread through phishing schemes involving email attachments or downloads (as in my case) and installs on an endpoint through website compromises. Some also engage malvertisements to welcome you into the butchery. If you think these old ways are too inadequate, consider this 2015 Verizon data breach report (C/O McAfee labs).
Clearly, Almost one out of four recipients open phishing messages and, shockingly, more than one out of 10 click on attachments to phishing messages. In addition, nearly half of all recipients open phishing emails and click on the links within the first 60 minutes of receiving the emails. What is very evident is that the “human operating system” is still the weakest link and need some serious patches.
The second step is infection. The downloaded binary arrives on the user’s computer and starts the processes it needs to complete its malicious activities.
CryptoWall 3 would generate a unique computer identifier, Ensure “reboot survival” by installing the program to run at start-up (through service entry, scheduled task, AutoRun key, etc.). Deactivate shadow copies, start-up repair, and Windows error recovery. Stop Windows Security Center, Windows Defender, Windows Update Service, error reporting, and BITS. Inject itself into explorer.exe and svchost.exe (for now just know these are very important files needed by the OS for optimum functionality). I would then retrieve the external IP address. Ransom32, the world’s first ransomware written in JavaScript had far much devastating method of infection. Watch out for the WannaCry to understand how WannaCry would have done this.
The third step is communications. The ransomware process will talk to encryption-key servers to retrieve the public key needed to encrypt data. CryptoWall 3, for example, connects to a compromised WordPress site and reports its status. All control server traffic is encrypted using the RC4 encryption algorithm.
The fourth step is file search. The ransomware process searches for files on the system in a systematic fashion. It typically looks for files that are important to the user and cannot be easily replicated, such as files with extensions of jpg, docx, xlsx, pptx, and pdf. You won’t believe the number of extensions WannaCry can encrypt.
The fifth step is encryption. This is typically done through moving and renaming the targeted files, then encrypting and renaming the files after a successful encryption.
The sixth and final step is the ransom demand, typically through taking over the screen of the infected endpoint and demanding payment. Messages such as below for WannaCry will be displayed on the screen.
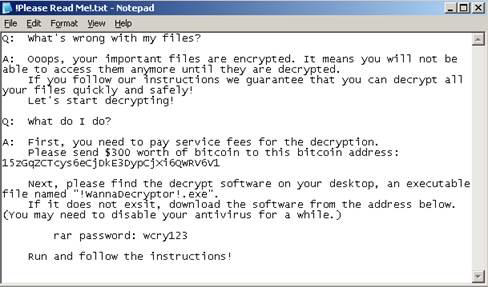
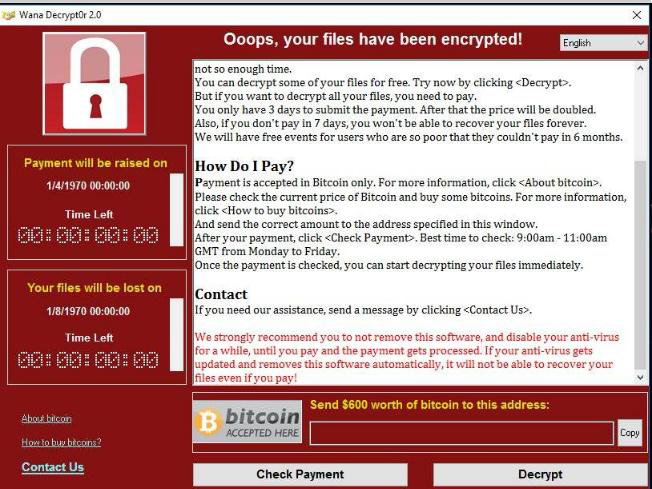
Then you will have to pay for the ransom, get a key from your own resources (e.g. deepweb), or wait for a key to be released by the serious security firms worldwide. But a problem statement still exists here; how could the ransom be paid without exposing the malware author to risk? Send payments to a post office box? Use e-wallets like PayPal? Or would you use M-Pesa? Ask the “AIDS” Trojan ransomware author who tried the post office method and law enforcement officials tracked the money and arrested him (then was very early, no secretive payment methods existed). But now this problem has been flipped upside down. A whole new world of digital currencies exist. I would not spend any of my time trying to break down this cryptocurrency world for this was already done in an earlier article. In a nutshell, they use Cryptocurrencies such as bitcoin. This video would help you understand briefly Bitcoin mining, the process involved in solving an algorithm to generate bitcoin. Another latest advancement in ransomware designs is that they will engage your computer resources to help solve the algorithm for generating the Bitcoin.
Hopingly this article has aided you in understanding what a ransomware is. Knowledge unapplied is knowledge not gained, and this is exactly why people with effective knowledge succeed while those with the knowledge and papers to prove so, but do not apply this knowledge fail. It is because of this that we (Me and you) will apply this knowledge to analyse the WannaCry ransomware in the next article. How else can I know if this work helped you if I don’t receive your comment?