Phishing attacks-the dangers of humble appeal
Published on May 01,2017

General introduction
If you appreciate that a humble human can become a hot-blooded witch, then you know the dangers of humble appeals. Often soothing by nature simply because most of them appeal to your inner self.
It is also by this technique that crime has and will continue to advance. An existing reproduction of such scenes takes you back to phishing. It is often the common denominator for most cyber threats.
In most scenarios, it is mitigated through the most powerful attack method, one that the latest software updates cannot patch.
Malicious hackers use it to deliver dangerous software (malware) and steal your personal information, which is later used to drain your account to zero.
If you have never been a victim (albeit very unlikely), don’t hero yourself by ignoring this knowledge base. Prevention is the precursor of cure. It is of interest to me to pass this knowledge to you and you to your friends and enemies. So keep engulfing the knowledge.
Phishing is using fraudulent email, websites, text messages and phone calls to trick people into disclosing personal financial or identity information, such as credit card or Social Security numbers, user names (e.g., NetID) and passwords that can later be used to access otherwise protected data.
As can be seen, it has spread its wings of propulsion up to and including your personal ways of communication. And that is where its success begins, where you are highly susceptible to failure.
It will be impossible to discuss each propulsion mode in one article and simultaneously give you adequate information about the same; for this reason, I will subdivide this information into various parts.
In this part, I will discuss the most common form of this attack. Hopefully, you will follow throughout the series.
Part 1: -Email Phishing
Email as a communication tool can be said to be the global communication infrastructure in corporations and businesses.
If you were to count the number of businesses or just personal colleagues using email, it would be, on a scale of 1 to 10, a 9.
Email provides us with a convenient and powerful communications tool, yet it also provides scammers and other malicious individuals an easy means for luring potential victims.
These attempted scams run from the old-fashioned bait-and-switch operations to phishing schemes using a combination of email and bogus websites to trick victims into divulging sensitive information. You need to know both of these techniques to stay on board and away from the sharks.
I will first explore the old-fashioned baits though they still work effectively.
Ideal business opportunities.
I will bet that a promise of an opportunity to make a great deal of money with very little effort will melt your low-melting-point heart. Especially if you are a desperate college student or a graduate hungry for money.
They don’t have to do it the hard way. There are scams meant entirely for this; believe me, they will catch up with you.
They’re normally full of enticements such as “Work only 2 hours a week and earn hundreds of dollars,” “Be your own boss,” “Set your own working hours,” and “Work from home.”
The subject of the emails may even smell sweeter honey; “Make a Regular Income Online” or “be the rich internet kid”.
In most cases, the email gives very little detail about the nature of the business opportunity. Most provide an address or website from which you can, for a fee, obtain an “information kit” about the opportunity.
These opportunities, however, usually amount to nothing more than pyramid schemes in which the “opportunity” involves your ability to recruit more unsuspecting people to buy into the scam. Eventually, the scam is uncovered, or the pool of new recruits runs dry, and it fails.
Health and diet scams.
These are like the lioness unto an antelope. They prey on the insecurities some people have about the state of their well-being. Consider the examples below.
- Reduce body fat and build lean muscle without exercise.
- Increase Your Sexual Performance Drastically.
- Natural Health Remedy That Gives energy and burns fat. It Works!
- Need to lose weight for summer?
These insecurities are so effective at making some people particularly susceptible to the scams because they may be reluctant or embarrassed to discuss their problems with a doctor, or they can’t afford to buy legitimate drugs or treatment.
The scams attempt to lure consumers with promises of quick fixes and amazing results, discount pricing, fast delivery, waived prescription requirements, privacy, and discreet packaging. Though customer testimonials may back them, beware: the products don’t work.
Huge discounts on software offers.
These scams frequently consist of advertisements for cheap versions of commercial software like Windows 10, Adobe Photoshop, Illustrator, or antivirus software like avast.
The discounts offered may be hard to believe, and with good reason: the scammers either do not deliver the promised software at all or provide illegal, pirated versions preloaded with Trojan horse software the scammer or other malicious individuals can use to exploit your computer and the information it contains.
The cheaper the thing, the more expensive the result for using it.
And now to more advanced techniques.
General phishing Email
Phishing emails are crafted to look as if they’ve been sent from a legitimate organization. These emails attempt to fool you into visiting a fake website to either download malware (viruses and other software intended to compromise your computer) or reveal sensitive personal information. The perpetrators of phishing scams carefully craft fake websites to look like the real thing.
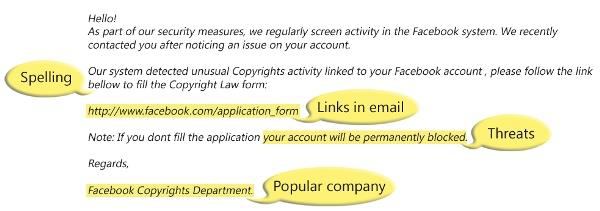
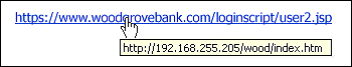
Some of them, like the above example, have links. Before you click the link. Rest your mouse (but don’t click) on the link to see if the address matches the link that was typed in the message. The example below shows that the real web address is not the same as the one typed.
Some of them also contain threats that are used as a tactic to scare you into opening your email to “protect” your account from further breaching. If the humble plea didn’t convince you, then the threat will.
For instance, an email can be crafted to look like it is from a major bank.
It might have an alarming subject line, such as “Problem with Your Account.”
The body of the message will claim there is a problem with your bank account and that, to validate your account, you must click a link included in the email and complete an online form.
But be in the know and carefully examine any email from your banks and other financial institutions. Most banks have instituted policies against asking for personal or account information in emails, so you should regard any email making such a request with extreme scepticism.
Trojan Horse Email
Like the old crafted Trojan horse (in Greek mythology)used to hide Troy soldiers into a successful ambush against the Mycenaean soldiers, a Trojan horse email offers the promise of something you might be interested in—an attachment containing a joke, a photograph, or a patch for a software vulnerability.
When opened, however, the attachment may do any or all of the following:
- create a security vulnerability on your computer to open a secret “backdoor” to allow an attacker future illicit access to your computer
- install software that logs your keystrokes and sends the logs to an attacker (key logger), allowing the attacker to sample out your passwords and other important information
- install software that monitors your online transactions and activities Provide attacker access to your files and turn your computer into a “bot” an attacker can use to send spam, launch denial-of-service attacks, or spread the virus to other computers.
Consider a case study of the “Love Bug” virus, attached to an email with the subject line “I Love You”, which asked the recipient to view the attached “love letter.”
Be keen on the following: email posing as a virtual postcard, email masquerading as a security bulletin from a software vendor requesting the recipient apply an attached “patch”, email with the subject line “funny” encouraging the recipient to view the attached “joke”, an email claiming to be from an antivirus vendor encouraging the recipient to install the attached “virus sweeper” free of charge.
Virus-Generated Email
Note that, in some cases, a familiar “from” address does not ensure safety: Many viruses spread by first searching for all email addresses on an infected computer and then sending themselves to these addresses.
So, if your friend’s computer has become infected with such a virus, you could receive an email that may, in fact, come from your friend’s computer but which was not actually authored by your friend.
If you have any doubts, verify the message with the person you believe to be the sender before opening any email attachments.
Generally, consider the following:
- Do not click on links, download files or open attachments in emails from unknown senders.
- It is best to open attachments only when you expect them, even if you know the sender.
- Never email personal or financial information. You never know who may gain access to your email account.
- Never enter personal or company information into a pop-up screen.
- Check your online accounts and bank statements regularly.
- Always treat your email password like the “keys to the kingdom” because that is what it is to spammers/hackers.
- Don’t make passwords anything personal. If the spammer/hacker has your name, it is easy to find out those details from social media.
- If you know the sender of an email, be hesitant. If you don’t know the sender, delete the email or check it with your IT department.
After an attacker successfully tricks you into clicking a link, you are often taken to a website to complete your anticipated gift. It is surprisingly easy to tell a fake website from a genuine one. In part two of the series, I will tell you how.