Phishing attacks - What is Web spoofing?
Published on May 06,2017
A complete phishing attack involves three roles of phishers.
As discussed in the first article, mailers send out many scam emails (usually through infected computers controlled as a group: botnets), which direct users to fraudulent websites.
Secondly, collectors set up fraudulent websites (usually hosted on compromised machines), which actively prompt users to provide confidential information.
Finally, cashers use confidential information to achieve a payout. In this article, we shall focus on the second step, the fraudulent websites.
A phisher could forge a website that looks similar to a legitimate website so that unsuspecting victims may think that it is a genuine website and enter their passwords and personal information, which is collected by the phisher.
With the advancements and simplicity of web development languages such as HTML, front-end codes can simply be cloned to achieve the look of a particular website. A little bit of web programming in Html and/or PHP is necessary to redirect the user's input into a file or database and then show a “website under maintenance" notice.
Some proxy software, such as squid or Fiddler2 could be extended to create a fully functional clone. Users can successfully sign in and use all the services provided by the original website while the server collects all the inputs, and the server may modify all the pages.
Once a forged website is online, the phisher must make potential victims visit it, and there are very many ways to achieve this.
- As discussed in the first article, they may send spoofed emails with a link to the forged website.
- Register a domain that is a common typo of a popular website. For example, register paypel.com and create a forged paypal.com.
- Register the same domain name in a different top-level domain (TLD). Sometimes people will type in their country-specific TLD and expect to get a “customized local" version of the website. For example, register gmail.com.ke and create a simplified-Kenyan forged version of gmail.com.
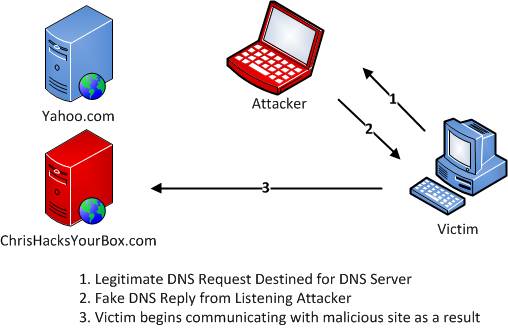
- Using pharming
Built-in security indicators
Modern web browsers, however, have certain built-in security indicators that can protect users from phishing scams, including domain name highlighting and HTTPS indicators. However, they are often neglected by users.
Domain name highlighting
Consider the following images.


The above-highlighted domains show that they are different sites.
Phishers tend to use misleading addresses, such as https://www.etax.go.ke, instead of the correct https://www.itax.go.ke to deceive users.
Domain name highlighting can save you. The idea behind it is simple: the domain name of an address is highlighted in the address bar so that users can inspect it to determine a website's legitimacy.
With domain name highlighting, users can easily interpret the address and identify the current website at a glance. Most web spoofing attacks can be identified unless the phisher is using pharming.
Browser security indicator: HTTPS padlock
A padlock icon appears in the address bar when visiting an HTTPS website.
HTTPS is a combination of Hypertext Transfer Protocol and Transport Layer Security. It provides encryption and identification through public key infrastructure (PKI), a technical technique for sharing encryption keys.
Modern web browsers display a padlock icon when visiting an HTTPS website. This technique, however, is not as effective as you might think.
Almost all security indicators commonly used by browsers to indicate a “secure connection” can be spoofed. Research shows that it is almost impossible to design a static indicator that cannot be copied under any domain name without HTTPS.
Dynamic skins can also be a good method. The idea is that the website server generates a unique abstract image for each user, and the web browser also independently computes the same image. The algorithm ensures that a phisher cannot predict this image. The user just needs to compare these two images; if they are identical, the server is legitimate.
Security and its other side, insecurity, are concepts that continuously evolve. So within a short span of time, even the measures we have will be overcome. For now, even if there is no surest way to ensure website security is non-vulnerable to spoofing, we should embrace the few measures we have to help curb the malice.