Has your password been leaked?
Updated on October 15,2022
Allow me to begin with the literal definition of a password. A password is a string you use for validation in order to access a given resource (may....
Read More
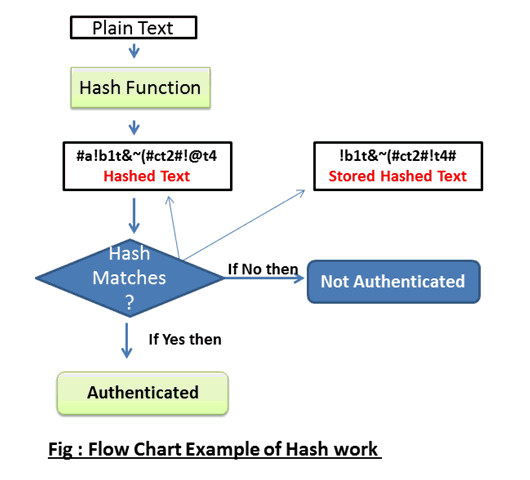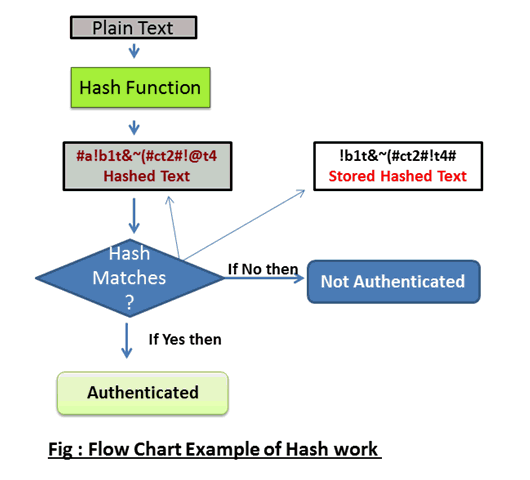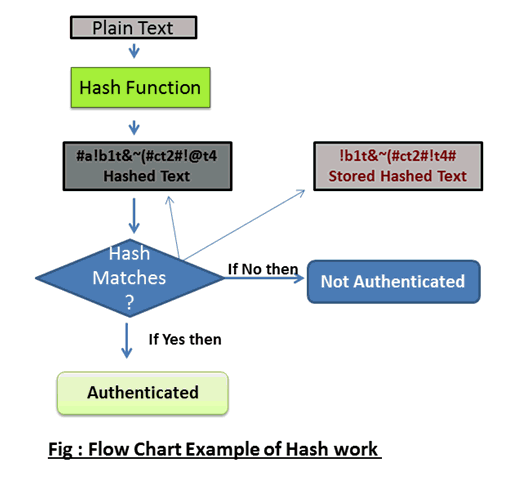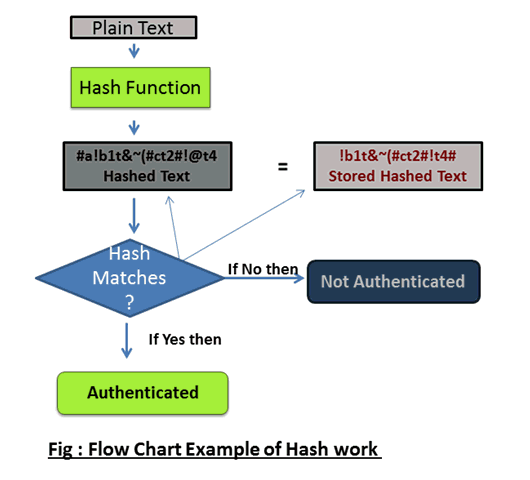
Updated on October 15,2022
Allow me to begin with the literal definition of a password. A password is a string you use for validation in order to access a given resource (may....
Read More
Updated on October 15,2022
It’s amazing what technology can do. Just a click away is the world’s largest collection of knowledge. Knowledge that, if used wisely,....
Read More
Updated on November 05,2022
For your company to ensure its viability and continuity throughout this age of technological revolutions, the 'telepresence of services' has to be....
Read More
Updated on October 23,2022
Code named ‘WannaCry’, ‘WannaDecryptor’, ‘WannaCrypt’ or just the layman’s ‘YouDontWannaCry’,....
Read More
Updated on October 15,2022
No one wants to be part of a story such as mine that follows. In January 2017, my computer screen was defaced with a very funny (yet annoying) begg....
Read More
Updated on October 15,2022
“Delete does not mean delete!” And if the aforementioned statement leaves you in a self-quagmire, upon reading this article, you will u....
Read More